#Backup monitoring
Explore tagged Tumblr posts
Text
How Backup Monitoring Tools Help Prevent Ransomware Attacks?
Ransomware attacks are serious threats to businesses of all sizes; they encrypt or take your data hostage and ask for a costly ransom. To guard against ransomware, the simplest way is to have secure and continuously monitored data backups.
Backup monitoring tools are important to protecting data as they help you keep an eye on what's unusual, what's right and not, what's not backing up, and give you early warnings of potential threats.
It detects Anomalies and Suspicious Activities
Backup monitoring tools are able to analyze patterns in backup activities and data access to check for patterns that might suggest an infection with ransomware. The software flags any abnormal patterns or activities and alerts IT teams for investigation before ransomware has had a chance to spread across the network.
Measures Backup Health and Completeness
Backup monitoring tools simply monitor the health and completeness of backup data over and over. If, for example, you’re hit by ransomware, the integrity of your backups is key to getting your data back. Therefore, backup monitoring is as important to ensure you have a backed-up, clean, recent copy of your data.
Supports Immutable Backups
Immutable backups are those types of backups that you cannot delete or modify once it has been created, and many backup monitoring tools support that. Ransomware protection also requires this feature because even if ransomware infects your system, it can’t overwrite or encrypt immutable backup copies.
The attack won’t touch these backups; they remain untouched and are a safe fallback you can restore from if your site is ever attacked.
Provides Real-Time Alerts and Automated Responses
Every second when ransomware tries to encrypt files or to interfere with backups, backup monitoring tools can provide real time alerts immediately. Some advanced tools can also develop automated responses including isolating knocked systems or stopping backup processes that may spread the problem.
Enables Detailed Audit Trails for forensic analysis
Backup monitoring tools keep formal logs of all the backup activities, attempts to access the backup site, as well as any change to the system. The audit trails of these logs can be extraordinarily useful in forensic analysis of a ransomware incident in establishing the origin of the attack and the security posture which contributed to the vulnerability.
Conclusion
In short, any ransomware defense strategy needs to include backup monitoring tools. Features like detecting suspicious activity, ensuring backup integrity, issuing real-time alerts, and maintaining detailed audit logs are enough to prove that.
0 notes
Text
Maximizing Potential: The Key to NetApp Monitoring Excellence
Data storage and management are necessary for business companies in today's fast-paced technological world. NetApp monitoring is vital in assisting businesses with efficiently storing, monitoring, and retrieving their data.
This article mentions 8 of the most important points to help you get the most out of NetApp monitoring and improve your data management strategy.
Customizable Dashboards
Customizing monitoring dashboards to fit specific organizational requirements improves visibility and makes data interpretation easier. Customizable dashboards enable administrators to concentrate on important metrics, simplifying the analysis of trends and performance indicators.
Automated Reporting
Consistent reporting is crucial for monitoring progress over time and making well-informed choices. Monitoring backup tools offer automated reporting capabilities that save time and effort. Administrators can easily gain comprehensive insights into system performance without requiring manual data compilation.
Capacity Planning and Forecasting
It is important to clearly understand your current storage usage and predict your future requirements to ensure smooth operations. Good NetApp monitoring tools should have strong capacity planning features, allowing organizations to allocate resources effectively and prevent unexpected storage shortages.
Multi-Cluster Monitoring
For organizations with intricate infrastructures across multiple clusters, it's important to have a NetApp monitoring solution that can easily monitor and manage all the clusters from one central interface. This guarantees a consistent perspective of the entire storage setup.
Predictive Analytics
Using predictive analytics can assist in foreseeing possible problems in advance. NetApp monitoring tools use advanced analytics to analyze past data and predict performance issues, helping to solve problems before they occur.
Resource Optimization
Monitoring tools should not just find problems but also provide suggestions for improving resource usage. This provides recommendations for reallocating storage, optimizing configurations, and adjusting settings to improve the efficiency of NetApp systems.
Compliance Monitoring
Many organizations prioritize meeting regulatory requirements. Effective NetApp monitoring solutions should have features that help monitor and ensure compliance with industry regulations, protect sensitive data, and prevent legal issues.
Scalability
As companies expand, their data systems also grow. NetApp monitoring tools must handle more data and storage systems as they grow. Scalability guarantees that the monitoring solution stays efficient as the organization grows its IT infrastructure.
Conclusion
It is important to fully utilize NetApp monitoring to achieve the best possible data management and storage efficiency. With the rapid advancement of technology, organizations need to invest in NetApp monitoring solutions. These solutions can provide a strategic advantage by helping organizations maximize their data infrastructure.
0 notes
Text
5 Easy Ways To Improve Salesforce Data Backup Recovery Strategy
In today's data-driven world, businesses rely heavily on Customer Relationship Management (CRM) systems like Salesforce to manage their customer information, track sales, and drive growth. However, even the most robust platforms are not immune to data loss or system failures. That's why having a solid Salesforce data backup and recovery strategy is crucial for ensuring business continuity. In this blog post, we'll explore five easy ways to enhance your Salesforce data backup and recovery strategy.
Regularly Scheduled Backups:
The foundation of any effective data recovery strategy is regular data backups. Salesforce provides a built-in data export tool that allows you to export data in a structured format, such as CSV or Excel. Set up a routine schedule for these exports to ensure that your data is backed up consistently. Depending on your organization's needs, you may choose to perform daily, weekly, or monthly backups.
Automate Your Backups:
Manually exporting data can be time-consuming and prone to errors. To streamline the process, consider automating your Salesforce data backups using third-party backup solutions. These tools can schedule and execute backups automatically, ensuring that your data is consistently and reliably backed up without manual intervention.
Store Backups Securely:
Backing up your Salesforce data is only half the battle. Equally important is where you store those backups. Utilize secure and redundant storage solutions, such as cloud storage platforms like Amazon S3 or Google Cloud Storage. Implement encryption and access controls to safeguard your backups from unauthorized access.
Test Your Recovery Process:
Having backups is essential, but they're only as good as your ability to recover data from them. Regularly test your data recovery process to ensure that it works as expected. Document the steps, and make sure that your team is familiar with the recovery procedures. Conducting mock recovery drills can help identify and address any potential issues before they become critical.
Monitor and Alerting:
Proactive monitoring is key to identifying data backup and recovery issues early. Implement monitoring and alerting systems that notify you of any backup failures or anomalies. This way, you can take immediate action to rectify issues and minimize data loss in case of a failure.
Consider Salesforce Data Archiving:
As your Salesforce database grows, it can become challenging to manage large volumes of data efficiently. Salesforce offers data archiving solutions that allow you to move older or less frequently accessed data to a separate storage location. This can help reduce storage costs and improve system performance, making your data recovery strategy more manageable.
In conclusion, enhancing your Salesforce data backup and recovery strategy doesn't have to be complicated. By implementing these five easy steps, you can significantly improve your organization's ability to recover critical data in the event of data loss or system failures. Remember that data is the lifeblood of your business, and a robust backup and recovery strategy is your insurance policy against unforeseen disasters.
#Salesforce best practices#Data loss prevention#Backup automation#Data retention policies#Data encryption#Salesforce customization#Data recovery testing#Backup monitoring#Data recovery procedures#Data backup optimization#Salesforce data protection#Backup reliability#Data restoration#Backup storage solutions#Data backup documentation#Salesforce metadata backup#Data backup strategy evaluation#Data backup policies#Salesforce data backup best practices
0 notes
Text
//I think about this off and on sometimes but the idea of Lambda referring to himself as a something sometimes and not a someone and not quite catching himself before it can slip out.
#backup log {ooc}#//is it a bit of the self hatred? yes#//but i do think it's partially him stepping back and being like 'huh. that it is?' and coming to a very not so great conclusion about-#//-his experiences#//i think i've got a mini story kicking around on my computer that goes into it a bit but the tl;dr of that story is him being like-#//-'if you're allowed to be people then you get to be a someone if you're not then you're a something. and somethings get to be monsters'#//or something like that it's kind of old so i don't really remember much of it right now#//it's that little bit that seeps out when he isn't monitoring/self policing himself#//idk it's something that's this bizarre mix of self hatred and being like kind of happy(?) that he doesn't have to deal with that in a-#//-sense? at least for him? idk a lot of mixed emotions there and this sounds silly as hell without much context but trust me it's sort of-#//-there? just roll with it
7 notes
·
View notes
Text
Today's show was so overhwelmingly chaotic that I had to use my inhaler TWICE (I've been trying to only use it once a day to see how my lungs are doing). But as chaotic and exhausting as it was... Goddamn I'm good at what I do.
While they were diagnosing a problem and working through Plan A, I set up Plan F by myself while 6 people stood around watching Plan A-C fail.
And when they yelled that the show would have to be canceled this week, I had Plan F up, set, running, and it was what I told them to do from the start.
Why is there only Plan A-C, then suddenly Plan F?
My Plan was always Plan F, for "Fuck it, we bail".
#i deserve this peanut butter cookie goddammit#the teleprompter system that's been failing for MONTHS finally kicked the bucket just before we were to film the show#and by the time they finally admitted it couldn't be saved i already had a backup system running#with the script fully loaded and formatted into a teleprompting software on my PC and had set up a monitor under the camera#it didn't have to be chaos but why tf did it take 6 people to watch 2 idiot engineers realize#they couldn't save THE COMPUTER THAT STILL RAN ON WINDOWS VISTA
11 notes
·
View notes
Text
okay, to be completely sure i post it here for Bubbs.
Gehog very quick reference in few minutes
for fun
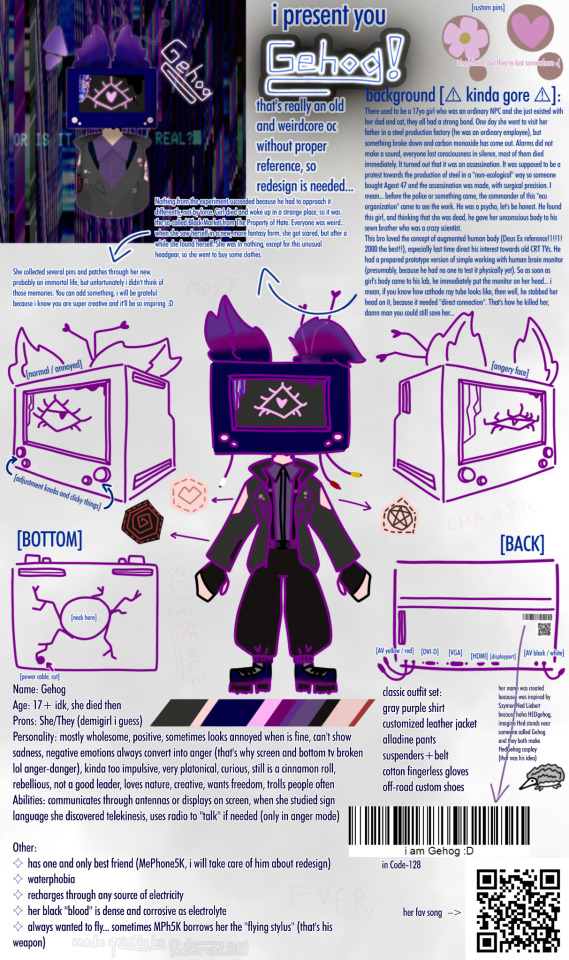
for fun....
#gehog#panterus2019#frau panteruz#frau panterus#gehog oc#hedgehog#szymon hed liebert#oc reference#chaotic oc#weirdcore#weirdcore oc#backup post#too lazy to remaster properly#tpoh inspired#tpoh oc#still working on it#tv head#tv girl#crt tv#crt monitor#fluffy ears#cinnamon roll#funny barcode#qr code#funny song#Agent 47 mentioned#gehog reference#quick character reference#man im tired#Bubbs
6 notes
·
View notes
Text
i swear to god if my computer doesn't start working properly again
i have two jobs dependent on that fucking thing and yet it once again doesn't connect with the monitor
#i have current commission backups on my laptop but that's not my only job#also that fucking monitor is the only well color calibrated thing in the house
8 notes
·
View notes
Text
Discover top-quality laptops, computers, gaming accessories, tech gadgets, and computer accessories at Matrix Warehouse. Shop online or in-store across South Africa for unbeatable prices and nationwide delivery. Visit now!
#Laptops & Accessories#Desktop Computers#Smart Devices#Computer Hardware#Monitors & Projectors#Computer Accessories#Backup Power Solutions#Printers and Printer Toners#Networking Equipment#Computer Software
2 notes
·
View notes
Text
UPS (Uninterruptible Power Supply): Protezione Affidabile per il Tuo PC in Caso di Blackout
SKE 850VA/480W UPS Gruppo di Continuità per PC Router Modem UPS Gruppo Continuità UPS HL850 In un mondo sempre più connesso e dipendente dall’elettricità, la protezione dei nostri dispositivi elettronici è fondamentale, soprattutto in caso di interruzioni di corrente o sbalzi di tensione. Un UPS (Uninterruptible Power Supply) è uno strumento essenziale per garantire la continuità…
#Review#Unboxing#850VA/480W#Backup alimentazione#Blackout protezione#Data Center UPS#Enterprise UPS#Gruppo di Continuità#ion#lithium#lithium ion#Lithium-ion UPS#Protezione dispositivi elettronici#recensione#SKE#SKE Smart-UPS Ultra#Smart-UPS#Smart-UPS Ultra#Uninterruptible Power Supply#UPS#UPS 850VA/480W#UPS Management#UPS Monitoring
4 notes
·
View notes
Text
this is NOT the time for my drawing tablet to act up!!!!!!!!!!!!
#. its not too bad but i need it to survive July for artfight#anyway thank god my ipad still works so i have a backup plan#but no yeah im gonna have to save money in july as a safety net#right now my anxiety is at its highest on it i dont know if it will survive the year#WHICH is shocking its barely 2 years old#its because im constantly using it everyday as my main monitor lmao#look a talking muffin
3 notes
·
View notes
Text
Automated Disaster Recovery Solutions by Esconet Technologies
Esconet Technologies, based in New Delhi, offers comprehensive Automated Disaster Recovery (ADR) solutions designed to ensure business continuity and data integrity. Their services encompass Cold DR for cost-effective data backup, Hot DR for real-time data synchronization, and Application-Supported DR to safeguard critical applications like Active Directory and databases. With continuous DR monitoring, management operations, and partnerships with leading OEMs such as Dell Technologies, HPE, VMware, Veeam, and Microsoft, Esconet delivers robust and scalable disaster recovery solutions tailored to diverse organizational needs.
for more details, Visit- Esconet Technologies Automated Disaster Recovery Solutions page
#Automated Disaster Recovery#Business Continuity Solutions#Cold DR Services#Hot DR Solutions#Application-Supported DR#Data Backup and Recovery#DR Monitoring and Management#Esconet Technologies#Disaster Recovery New Delhi#IT Infrastructure Resilience
0 notes
Text
It's a Tech Kinda Weekend...
So, I have a PC and a laptop (and a Chromebook but whatever).
Both were Windows 10 when I got them, now upgraded to Windows 11. On Windows 10, you set a 4 digit pin. On Windows 11, you do 6-8 digit pins. But when it upgraded to Windows 11, all fine, it kept my pin.
An update came out the other day and I installed it on my laptop. Went to turn it on yesterday, and it asked for my pin instead of fingerprint (it's fine, it does that every month or so where it wants both in one login just to kind of re-verify).
And apparently it won't take my 4 digit pin anymore. It only wants a 6-8 digit pin. Which again, coming from windows 10 originally, I only ever had a 4 digit pin.
I ended up having to bitlocker my own laptop and completely reinstall the operating system, fully wiping my files and resetting to new, all because Windows 11 suddenly decided to force a 6-8 digit pin without letting me set one.
So, if you have a 4-digit login pin for your PC, go update it or you might face the same problem I did...
Today is less dramatic, I'm just upgrading my portable drive from 1TB to 2TB. So far I'm only moving the folder I keep shows in...
**I don't know why there are so many "Items" listed, I don't record THAT many shows...
Oh, it's because half of my watch-through posts were mistakenly put in that folder instead of the Screenshots one.
#I upgrade it every 5 years or so just to make sure I don't have a drive go bad and lose data#the laptop reset wasn't more than an aggravation issue- i keep everything on it cloud backup anyways#but i had to spend 5 hours between the reset and recovering old stuff#i have a bit of a neurotic stupidity where at WORK i have to constantly monitor drives and worry about space#2 TB left on a drive at work is like 'you have 1 month to get new drives approved or it's a disaster'#I have 8tb at home now and i'm barely using 10% of the space I have#and most of that 10% is everything saved on two different drives in case one crashes#i have a lot of space free and frankly i'm always wanting more#i'm like a dragon who hoards unused space
2 notes
·
View notes
Text

Happy Birthday AUTONNOMOUS
https://www.autonnomous.com/
0 notes
Text
Backups and Disaster Recovery | Innovative Computing Systems!

Our team of highly skilled and certified engineers will work with you to design a backup solution, build a Backups and Disaster Recovery plan, and validate that plan to ensure you are prepared for the worst. Our award-winning cloud-hosted backup platforms ensure that your backups are always available, safe, and secure.
Visit Now! https://www.innovativecomp.com/backups-and-disaster-recovery/
0 notes
Text
Simplify NoSQL Database Management with Simple Logic 🗂️
Database Optimization⚡ Enhance the performance of MongoDB, Cassandra, and more
Data Scalability📈 Seamlessly scale to meet evolving demands
Backup & Recovery🔄 Secure your data with robust recovery options
24/7 Monitoring👀 Proactively identify and resolve database issues
Partner with Simple Logic for NoSQL Success 📧 Email: [email protected] 📞 Phone: +91 86556 16540
#Database#DatabaseOptimization#DatabaseManagement#MongoDB#Cassandra#Data#DataScalability#Backup#Recovery#Monitoring#DatabaseIssues#SimpleLogicIT#MakingITSimple#SimpleLogic#MakeITSimple
0 notes
Text
Dark Web Monitoring

🔒 Safeguard Your Business in the Digital Age with Century Solutions Group! 🔒
🚨 Did You Know? The Dark Web is a hidden marketplace where stolen business data is bought and sold—and small businesses are prime targets!
Imagine this: A small online retailer gets hacked, and customer data is exposed on the Dark Web. The result? Loss of trust, reputation damage, and financial setbacks.
💡 How Can You Stay Protected?
🔍 Dark Web Monitoring – With Century Solutions Group, your business is constantly scanned for compromised data. If your credentials appear on illicit platforms, we alert you before the damage is done!
🛡️ Our Cybersecurity-First Approach Includes: ✅ Advanced Threat Protection – Firewalls, encryption, and AI-driven security. ✅ Employee Security Training – Your first line of defense is an informed team! ✅ Multi-Layered Defense – Strong passwords, MFA, and endpoint security. ✅ Secure Payment Transactions – Protect your customers & your revenue.
💼 Why Partner with Century Solutions Group? We’ve been Atlanta’s trusted IT MSP since 1996, offering cutting-edge cybersecurity solutions tailored for small businesses. Our proactive security approach means you can focus on growth—while we keep the bad guys out!
💪 Don’t wait for a cyberattack to react—stay ahead with Century Solutions Group! https://centurygroup.net/cloud-computing/cyber-security/
#CyberSafeBusiness #DarkWebDefense #CenturySolutionsGroup #MSP #SmallBizSecurity #CybersecurityAwareness
#Dark Web Monitoring#Cybersecurity#cybersecurity threats#data backup#Advanced Threat Protection#Employee Security Training#managed it services
2 notes
·
View notes